WIF involves lot of related concepts.
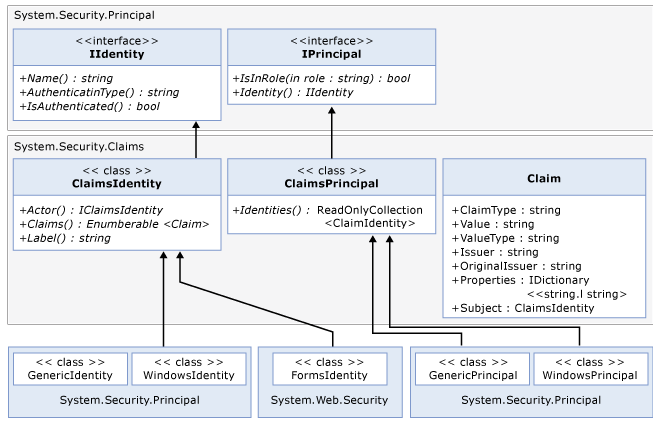
IIdentity
Usually represents the user. This interface is implemented by GenericIdentity and WindowsIdentity classes.
Identity Objects encapsulates information about the user or the entity. It basically contains a name and an authentication type. The name can be user's name or Windows account. .All Identity classes implement IIdentity interface.
IIdentity
Usually represents the user. This interface is implemented by GenericIdentity and WindowsIdentity classes.
Identity Objects encapsulates information about the user or the entity. It basically contains a name and an authentication type. The name can be user's name or Windows account. .All Identity classes implement IIdentity interface.
IPrincipal
IPrincipal represents the security context of the user. It has Identity property which returns identity of current principal.
Here's a class diagram of WIF, extracted from MSDN
IPrincipal represents the security context of the user. It has Identity property which returns identity of current principal.
Here's a class diagram of WIF, extracted from MSDN
- Managed code can discover identity or role of principal through Principal object. Principal object contains reference to an Identity object.
- You can compare Identity and Principal objects to similar concept like User and Group Accounts.
- In .NET, Identity objects represents users and roles represent membership and security context
- Principal object encapsulates both identity object and a role.
Represents a claim based identity. It is a concrete implementation of claim based identity (Identity described by a collection of claims) The Claims contained in a ClaimsIdentity describes a entity that identity represents and can be used for authorization and authentication decisions.
The ClaimsPrincipal has a Claims property as well. In majority of cases you should access users Claims through ClaimPrincipal.Claims collection.
ClaimsPrincipal (inherits IPrincipal)
An IPrincipal implementation that supports multiple claim based identities. It has Claims property (IEnumerable) which has claims from all claim identities associated with the claims principle.
If you're implementing your own identity or principal objects you should implement ClaimsPrincipal or ClaimsIdentity.
Accessing ClaimsPrincipal from HttpContext
Cast HttpContext.Current.User to a ClaimsPrincipal and access Claims
Claim
Claim is a piece of identity information. Usually you don't look up for claims. User delivers claims to your application. Claims are made by an issuer. Issuer can be your company therefore you trust the claims. Claim class has an issuer property which you can use to see who issued them.
Security Token
User delivers set of claims to your application with a request. Later this might be cached in a cookie to read for consequent requests. Security token is a serialized set of tokens that is signed by an issuing authority. The signature is important.
Issuing authority
This can be domain controllers that issue Kerberos tickets, authorities that issue X.509 certificates. Basically issuing authority is responsible to authenticate users for you.
Security Token Service
Service that builds, signs and issues security tokens (according to WS-Trust and WS-Federation protocols). There are pre-built token services such as ADFS, cloud STS such as Windows Azure Access Control service etc.
You can built your own STS to issue custom tokens using WIF.
Relying Party
When you are building an application that uses claims, you're building a relying party (RP) application. (claims aware application, claim based application etc.). RP uses claims to do identity related activities. WIF fully supports this
Resources
https://msdn.microsoft.com/en-us/library/hh873308(v=vs.110).aspx
Claim is a piece of identity information. Usually you don't look up for claims. User delivers claims to your application. Claims are made by an issuer. Issuer can be your company therefore you trust the claims. Claim class has an issuer property which you can use to see who issued them.
Security Token
User delivers set of claims to your application with a request. Later this might be cached in a cookie to read for consequent requests. Security token is a serialized set of tokens that is signed by an issuing authority. The signature is important.
Issuing authority
This can be domain controllers that issue Kerberos tickets, authorities that issue X.509 certificates. Basically issuing authority is responsible to authenticate users for you.
Security Token Service
Service that builds, signs and issues security tokens (according to WS-Trust and WS-Federation protocols). There are pre-built token services such as ADFS, cloud STS such as Windows Azure Access Control service etc.
You can built your own STS to issue custom tokens using WIF.
Relying Party
When you are building an application that uses claims, you're building a relying party (RP) application. (claims aware application, claim based application etc.). RP uses claims to do identity related activities. WIF fully supports this
Resources
https://msdn.microsoft.com/en-us/library/hh873308(v=vs.110).aspx











0 comments:
Post a Comment